Safehomepage.com is a browser hijacker that will alter your web browsers settings. It will change your home page and default search engine provider. It can also hijack your web browser shortcut and install additional software onto your computer. So, how do you recover from it if youve been hijacked? Read on as this article is going to take a look at exactly that.
First of all, browser hijacking is an irritating practice whereby malware and unscrupulous websites change your browser settings without your knowledge or permission. In other words the malware or website hijacks or kidnaps your browser. This is just as frustrating as it sounds because what this means is that you will be subjected to one, most or all of the following annoyances:
- Your browsers home page will have changed from the one that you usually use – for example Google, Yahoo or Bing – to one not of your choosing, in this case safehomepage.com
- The search engine that you use when browsing the web will suddenly start redirecting you to websites that you have no interest in visiting.
- Some of the other websites that you visit may also redirect you to different sites
- Your computer screen will very likely be flooded with a constant stream of pop-up adverts or advertising banners
- You may have had a strange tool bar installed on your browser which rather than adding any extra functions is annoying and unusable
- Your bookmarks or favorites folders may suddenly be populated with dozens, if not hundreds, of URLs to websites that you have never even visited, let alone saved as a favorite.
If your home page of choice has been hijacked and is forcing you to use a home page against your will then you naturally will want to resolve the issue. But how do you do that? First of all it’s useful to know how browser hijacking takes place.
Safehomepage.com will find its way on to your computer system along with freeware and fake installers. Fake installers are distributed in various ways. If you got a notification from a web page saying that your Flash player is outdated then you probably visited a bogus site promoting fake installers, read more
here. This browser hijacker is also promoted on various software download sites. Not the most popular ones but still with enough traffic to infection thousands of PCs in different countries. It is usually presented as an offer before the actual download begins.
This would be a good time to say that if you don’t have anti-virus, anti-spyware or another type of security software installed on your PC then you should do this as a matter of urgency. Having a reputable security program on your PC is your first and best line of defense against being infected by any of the numerous types of malware that are out there, not just browser hijackers.
So, you’ve run your anti-malware or other security program a couple of times and rebooted your PC or laptop but your home page and search engine are still redirecting you to safehomepage.com? This means that the problem could have been caused by an application which was installed without your knowledge or permission and that is hidden deep somewhere within your computer’s system. Please follow the removal instructions below, this hopefully will help you get rid of the hijack and restore your computer.
If you’re still having trouble, don’t panic – browser hijackers, including safehomepage.com, are designed to be as difficult as possible to find and uninstall so please leave a comment below and I will try to to help you. Good luck and be safe online!
Safehomepage.com removal instructions:1. First of all, download recommended anti-malware software and run a full system scan. It will detect and remove this infection from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this browser hijacker. Hopefully you wont have to do that.
2. Uninstall Safehomepage.com and related programs from your computer using the
Add/Remove Programs control panel (Windows XP) or
Uninstall a program control panel (Windows 7 and Windows 8).
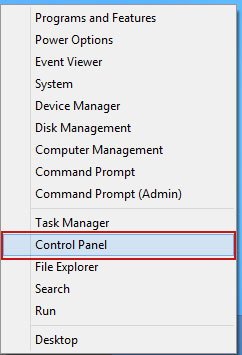
Go to the
Start Menu. Select
Control Panel →
Add/Remove Programs.
If you are using Windows Vista or Windows 7, select
Control Panel →
Uninstall a Program.

If you are using Windows 8, simply drag your mouse pointer to the right edge of the screen, select
Search from the list and search for "control panel".

Or you can right-click on a bottom left hot corner (formerly known as the Start button) and select
Control panel from there.
3. When the
Add/Remove Programs or the
Uninstall a Program screen is displayed, scroll through the list of currently installed programs and remove
QType,
eSave Security Control,
Safehomepage,
New Tabs Uninstall,
Desk 365,
BrowserProtect and any other recently installed application. As I said earlier, this application is rarely listed as Safehomepage in the currently installed programs list. So, either look for applications mentioned here or try to remember what software you installed recently. Its probably the culprit.
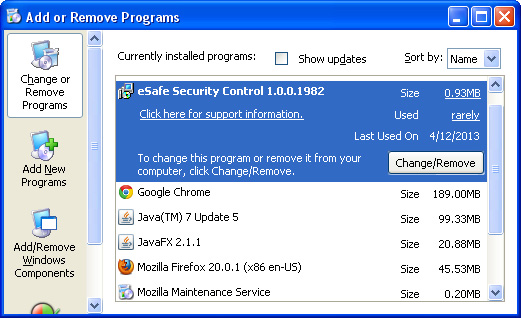
Simply select the application and click
Remove. If you are using Windows Vista, Windows 7 or Windows 8, click
Uninstall up near the top of that window. When youre done, please close the Control Panel screen.
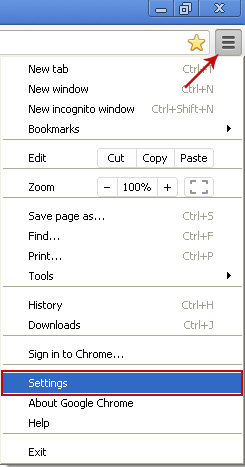
Remove Safehomepage.com from Google Chrome:1. Click on
Customize and control Google Chrome icon. Select
Settings.
2. Click
Set pages under the
On startup.
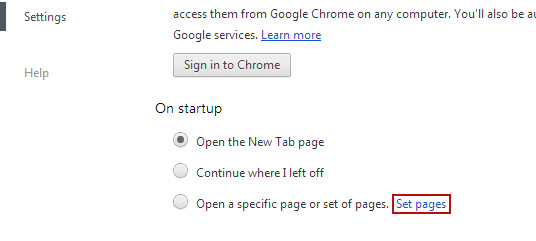
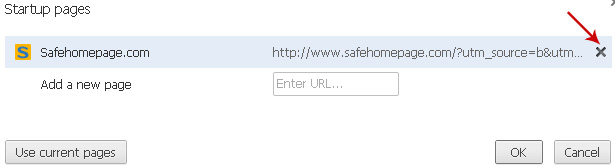
Remove
safehomepage.com by clicking the "
X" mark as shown in the image below.
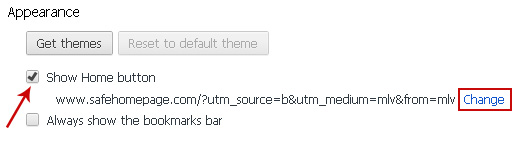
3. Click
Show Home button under
Appearance. Then click
Change.
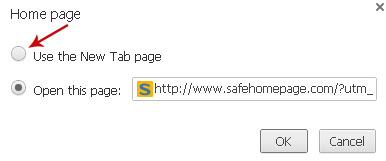
Select
Use the New Tab page and click
OK to save changes.
4. Click
Manager search engines button under
Search.
Select
Google or any other search engine you like from the list and make it your default search engine provider.
Select
Safehomepage.com from the list and remove it by clicking the "
X" mark as shown in the image below.
5.
Right-click the Google Chrome
shortcut you are using to open your web browser and select
Properties.
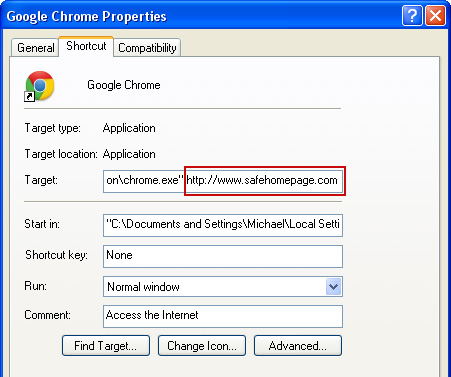
6. Select
Shortcut tab and remove "http://www.safehomepage.com...." from the
Target field and click OK to save changes. Basically, there should be only the path to Chrome executable file. Nothing more.
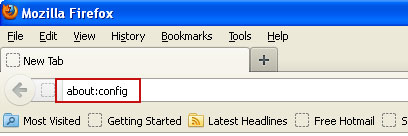
Remove Safehomepage.com from Mozilla Firefox:1. In the URL address bar, type
about:config and hit Enter.
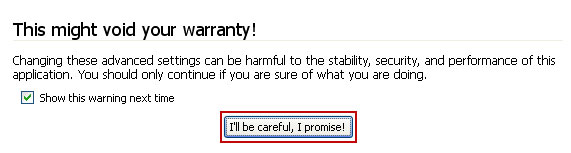
Click
Ill be careful, I promise! to continue.
In the search filter at the top, type:
SafehomepageNow, you should see all the preferences that were changed by safehomepage.com. Right-click on the preference and select
Reset to restore default value.
Reset all found preferences!You can also use the
Reset Firefox feature.
2.
Right-click the Mozilla Firefox
shortcut you are using to open your web browser and select
Properties.
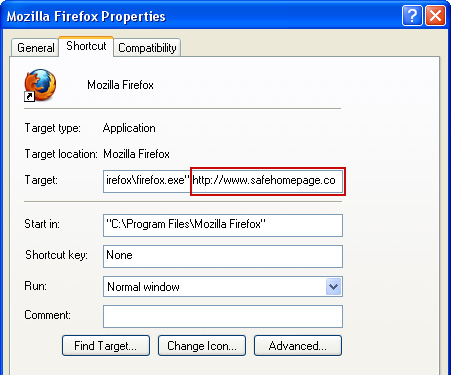
3. Select
Shortcut tab and remove "http://www.safehomepage...." from the
Target field and click OK to save changes. Basically, there should be only the path to Firefox executable file.
Remove Safehomepage.com in Internet Explorer:1. Open Internet Explorer. Go to
Tools →
Manage Add-ons.

2. Select
Search Providers. First of all, choose
Live Search search engine and make it your default web search provider (
Set as default).
3. Select
Safehomepage.com and click
Remove to remove it. Close the window.
4.
Right-click the Internet Explorer
shortcut you are using to open your web browser and select
Properties.
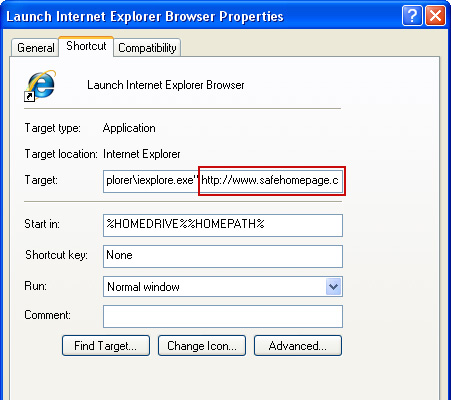
5. Select
Shortcut tab and remove "http://www.safehomepage.com...." from the
Target field and click OK to save changes. Basically, there should be only the path to Internet Explorer executable file.
6. Finally, go to
Tools →
Internet Options and restore your home page to default. Thats it!























 I love USB flash drives. I think these little suckers are one of the best things to hit computers since sliced bread. I used a flash drive almost every day this past semester of school and boy was it a nifty thing to keep around. Almost every piece of school work I had to do this past semester is on my trusty 2GB Toshiba flash drive.
I love USB flash drives. I think these little suckers are one of the best things to hit computers since sliced bread. I used a flash drive almost every day this past semester of school and boy was it a nifty thing to keep around. Almost every piece of school work I had to do this past semester is on my trusty 2GB Toshiba flash drive.




